3. Operator Responsibilities
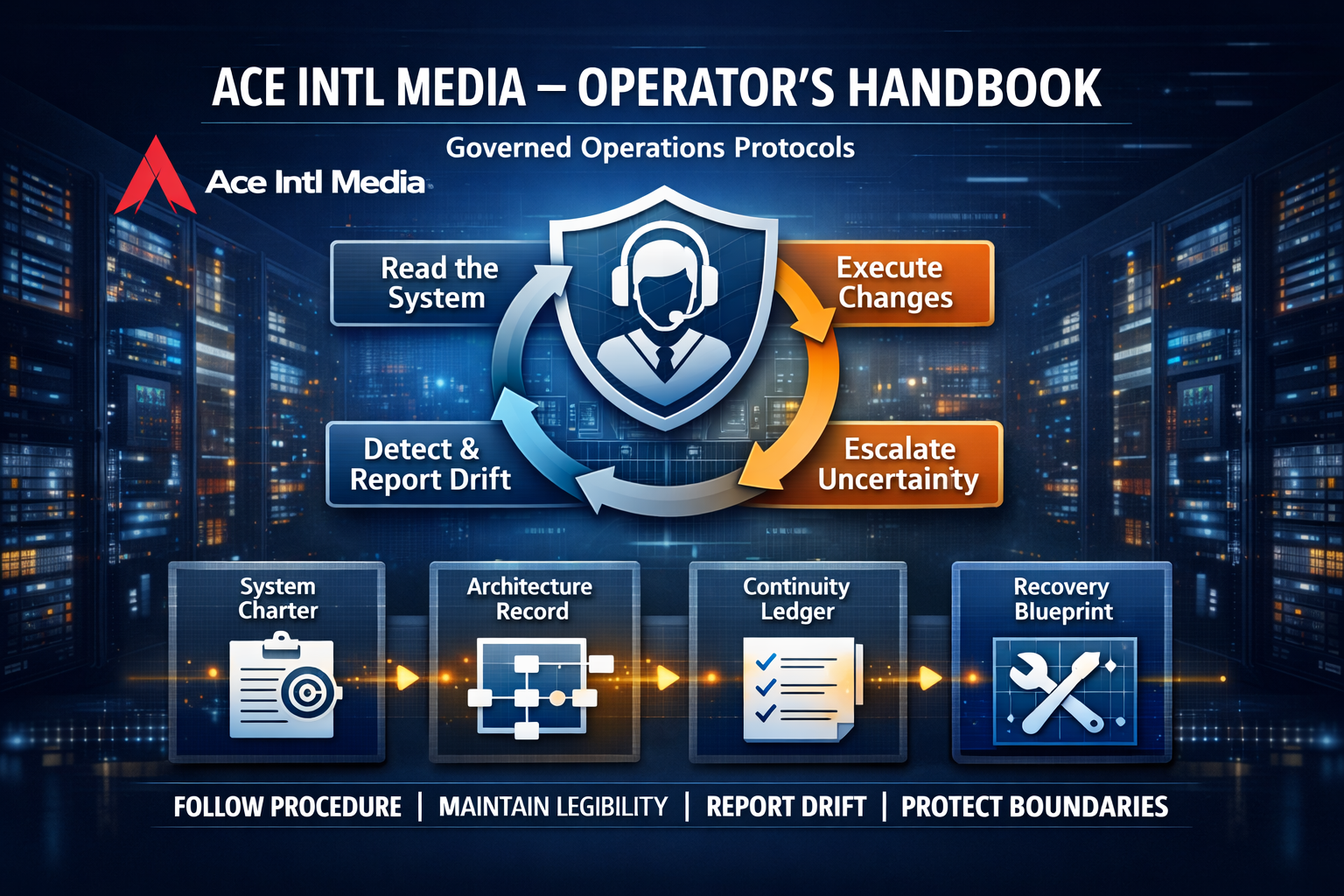
3.1 Understand the System Charter
The system charter defines system intent, boundaries, constraints, and
assumptions. It establishes what the system exists to do, what it must not
do, and which failures are unacceptable.
If the system charter is unclear, outdated, or incomplete, the operator
must stop. Action without charter clarity introduces unbounded risk and
architectural drift.
3.2 Follow the Architecture Record
Architecture records document design decisions, rejected alternatives,
dependency relationships, and known failure modes.
These records exist to prevent reinterpretation, reintroduction of rejected
approaches, and local optimisation that violates system intent. Operators
execute against architecture; they do not redefine it.
3.3 Maintain Documentation Currency
Documentation is operational work. Knowledge that exists only in memory is
considered volatile state.
- Update documentation before changes when intent is known
- Update documentation after changes when execution is complete
- Record deviations from expected behaviour
- Record observations discovered during operation
3.4 Execute Changes with Integrity
All changes must preserve boundaries, remain explainable, and maintain a
viable recovery path at all times.
Undocumented changes, shortcuts, or temporary fixes without reversibility
are violations, regardless of operational success.
3.5 Detect and Report Drift
Drift includes mismatched diagrams, outdated documentation, undocumented
dependencies, unexplained behaviour, and reliance on memory.
Drift is a present condition, not a future risk. Detection without
reporting is itself a failure and must be escalated immediately.