3. How the Network Is Structured
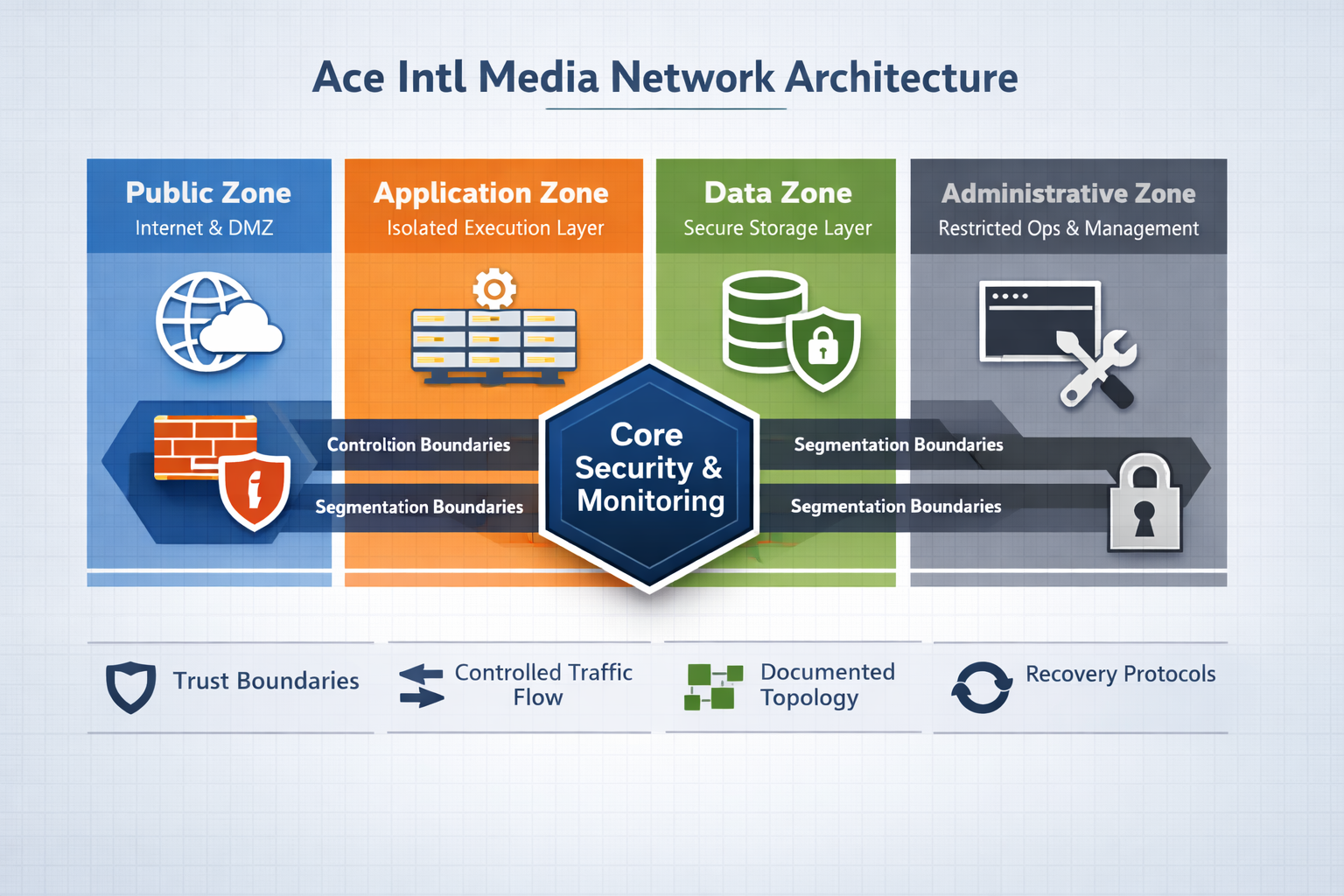
3.1 Segmented by Design
The network is intentionally segmented to reduce risk, preserve
predictability, and prevent uncontrolled propagation of failure.
Segmentation separates:
- public exposure
- application logic
- data storage
- administrative control
Each zone has a defined role and operates within enforced boundaries.
No zone implicitly trusts another.
3.2 Controlled Exposure
Only components that must be public are exposed.
Everything else is protected behind firewalls, identity layers,
and access controls.
Exposure is intentional, documented, and limited to necessity.
Accidental or inherited exposure is not permitted.
3.3 Documented Topology
The network topology is documented in a client-safe form that explains
structure, boundaries, and traffic flow without exposing internal
operational detail.
Topology documentation is published through the Network Index to
preserve transparency while maintaining security.