ACE INTL MEDIA — OPERATIONAL STANDARD
Rules governing day-to-day execution across the ecosystem, ensuring all
operational activity preserves architecture, continuity, and recovery
integrity.
This standard forms part of the publicly documented doctrine of the
Ace Intl Media Network, with organisational
context available at
aceintlmedia.com
.
1. Purpose
Operations are the daily movements of the ecosystem.
This standard ensures that every operational action:
- preserves legibility
- maintains continuity
- protects boundaries
- avoids drift
- supports recovery
- aligns with architectural intent
Architectural intent referenced during operations is defined in the
Architecture Standard.
Operations are not “tasks.”
Operations are the controlled execution of a governed system.
2. Operational Principles
2.1 Operations must reinforce structure
Every operational action must strengthen:
- clarity
- documentation
- boundaries
- recoverability
If an action weakens structure, it is prohibited.
2.2 Operations must be predictable
Operational behavior must be:
- consistent
- documented
- repeatable
- observable
Unpredictable operations introduce silent failure.
2.3 Operations must be reversible
Every operational action must be:
- traceable
- reversible
- recoverable
If an action cannot be undone, it must not be performed.
2.4 Operations must be low-risk by design
Operational processes must:
- minimize cognitive load
- minimize branching logic
- minimize dependency exposure
- minimize ambiguity
High-risk operations require architectural review as defined in the
Architecture Standard.
2.5 Operations must surface signals early
Operators must treat:
- hesitation
- uncertainty
- unexpected behavior
- undocumented dependencies
as structural signals, not operational noise.
3. Operational Roles
3.1 Steward
Responsible for:
- architectural alignment
- continuity integrity
- recovery readiness
- operational oversight
The steward is the final authority for operational decisions.
3.2 Operator
Responsible for:
- executing procedures
- maintaining documentation
- detecting drift
- escalating uncertainty
Operators do not modify architecture.
3.3 Contributor
Responsible for:
- performing scoped tasks
- following governed procedures
- respecting boundaries
Contributors operate under steward oversight.
3.4 Client Representative
Responsible for:
- providing clear intent
- validating requirements
- respecting governance
Clients do not perform operational actions.
4. Operational Requirements
4.1 Documentation Before Action
No operational action may occur without:
- current documentation
- validated boundaries
- confirmed recovery path
If documentation is missing, operations halt.
4.2 Evidence Capture
All operational actions must produce:
- timestamps
- commands or steps
- observed behavior
- deviations
- operator notes
Evidence is mandatory.
4.3 Operational Logging
Every action must be logged in the:
- continuity ledger
- operational log
- change record (if applicable)
Logs are governed by the
Continuity Standard.
4.4 Boundary Enforcement
Operations must not:
- cross architectural boundaries
- introduce new dependencies
- bypass governed interfaces
- modify system intent
Boundary violations trigger immediate review.
4.5 Dependency Awareness
Operators must understand:
- upstream dependencies
- downstream dependencies
- failure propagation paths
Unknown dependencies are treated as drift.
5. Operational Procedures
5.1 Standard Operational Procedure (SOP)
Every operational action must follow a documented SOP that includes:
- purpose
- prerequisites
- steps
- expected outcomes
- failure conditions
- escalation path
SOPs must be version-controlled.
5.2 Execution Protocol
Operators must:
- Validate documentation
- Validate boundaries
- Validate recovery
- Execute SOP
- Capture evidence
- Update documentation
- Verify continuity
Skipping steps is prohibited.
5.3 Escalation Protocol
Operators escalate when:
- behavior is unexpected
- documentation is unclear
- boundaries are ambiguous
- recovery is uncertain
- drift is detected
Escalation is immediate.
5.4 Deviation Protocol
If an operator must deviate from an SOP:
- deviation must be documented
- deviation must be justified
- deviation must be approved by the steward
- deviation must be reviewed post-execution
Unapproved deviations are violations.
6. Operational Surfaces
6.1 Approved Interfaces
Operations may only occur through:
- governed control surfaces
- portal interfaces
- approved tools
Governed interaction occurs via the
Ace Intl Media Portal
.
6.2 Observability Surfaces
Operators use observability to:
- detect drift
- validate behavior
- confirm boundaries
- identify anomalies
Observability is for understanding, not reassurance.
6.3 Communication Surfaces
Operational communication must occur through:
- portal channels
- designated operational channels
Informal communication is not operationally valid.
Operational Execution Model

7. Operational Risk Management
7.1 Risk Identification
Operational risk includes:
- undocumented changes
- unclear boundaries
- dependency failures
- operator uncertainty
- drift indicators
Risk is structural, not personal.
7.2 Risk Mitigation
Mitigation includes:
- halting operations
- escalating to steward
- updating documentation
- performing recovery tests
- performing architectural review
7.3 Risk Escalation
High-risk conditions trigger:
- continuity review
- recovery readiness check
- dependency audit
7.4 Operational Suspension
Operations may be suspended when:
- continuity is compromised
- architecture is threatened
- recovery is uncertain
- client behavior introduces risk
Suspension protects the ecosystem.
8. Definition of Operational Compliance
Operations are compliant when:
- they preserve legibility
- they follow structure
- they maintain documentation
- they avoid drift
- they respect boundaries
- they support recovery
- they reinforce continuity
Operations are not judged by speed.
Operations are judged by structural integrity.
These controls align with recognised standards including
ISO 22301
and
ISO 27001
,
without claiming certification.
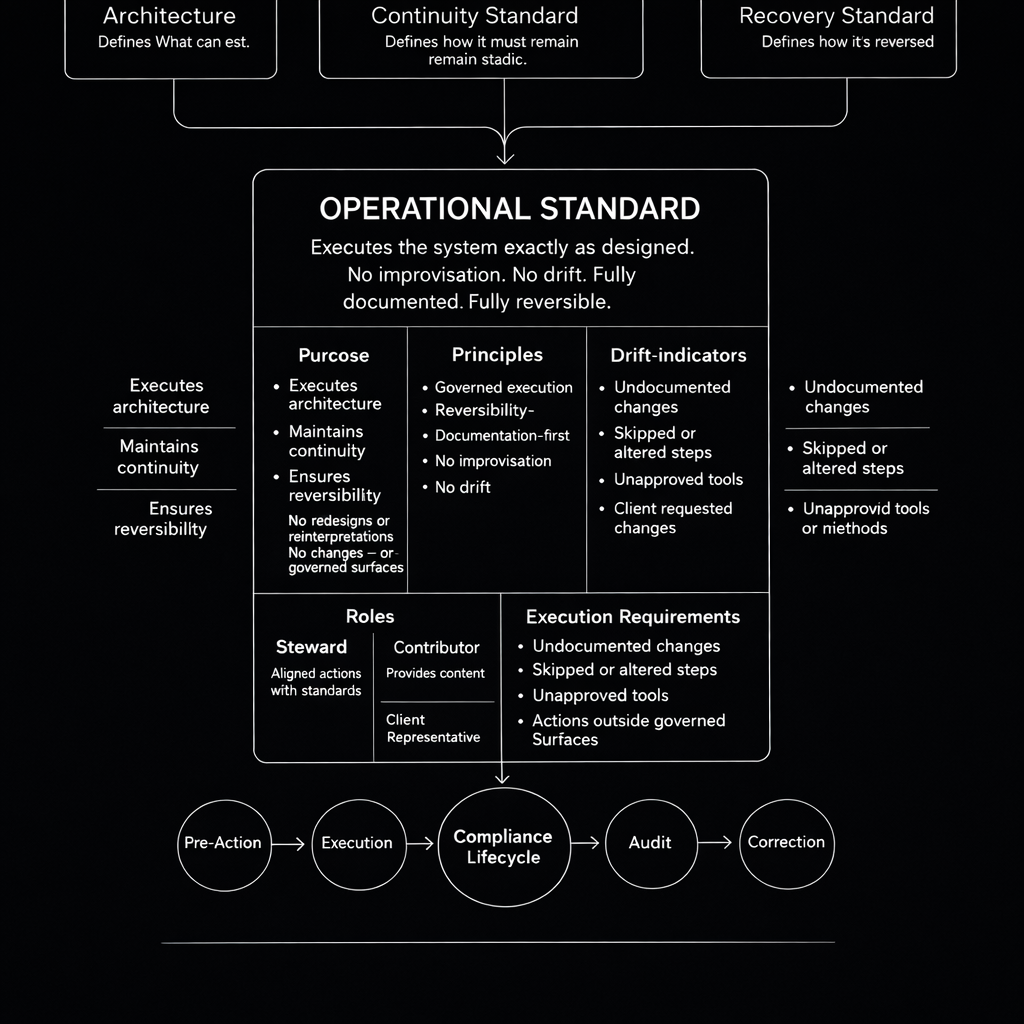
Operational Standard — Execution Model
The Operational Standard functions as the execution layer of the Ace Intl
Media doctrine. It ensures that systems are operated exactly as designed,
without improvisation, undocumented change, or uncontrolled deviation.
This model translates architectural intent into governed execution,
maintains stability under continuity conditions, and ensures full
reversibility during recovery events.
Operational execution is bounded by three controlling standards:
-
Architecture Standard — defines what may be built,
modified, or extended within the system.
-
Continuity Standard — defines how the system must remain
stable and legible over time.
-
Recovery Standard — defines how all actions must remain
reversible under failure or drift.
The Operational Standard does not reinterpret these rules.
It enforces them during execution.
This approach aligns with recognised operational and continuity frameworks,
including
ISO 22301
and
ISO 27001
,
without claiming certification.
Additional organisational context is available at
aceintlmedia.com
,
with related doctrine published across the
Ace Intl Media Network.
Operational Standard — Execution Model Diagram